SonicWall MySonicWall Cloud Backup Breach: Configs Exposed
SonicWall confirms a MySonicWall cloud backup breach exposing firewall configurations. Learn how to check impact, remove exposed backups, and reset all credentials.
Overview of the Incident
This breach was not a traditional CVE or software vulnerability but rather a compromise of SonicWall’s cloud infrastructure. Attackers performed a brute-force attack on the MySonicWall cloud backup API, ultimately retrieving backup configuration files (`.EXP`) from customer accounts. Initially, SonicWall estimated that less than 5% of customers were affected, but after a deeper investigation with Mandiant, it confirmed that 100% of cloud backup customers were impacted.
The exposed configuration files contain detailed network topologies, VPN settings, firewall rules, and encrypted credentials. SonicWall noted that encryption methods vary: AES-256 for Gen7 devices and 3DES for Gen6. Despite encryption, attackers can use these files to analyze environments and attempt offline password cracking.
Affected Systems
- All SonicWall firewalls that use the MySonicWall Cloud Backup feature.
- Devices running Gen6 and Gen7 firmware with configuration backups stored in the SonicWall cloud.
- Any credentials stored in these configuration files (local admin, VPN, LDAP, RADIUS, TACACS+, SNMP) may be compromised.
Exploitation Details
Threat actors targeted SonicWall’s cloud API directly, repeatedly attempting logins until successful access was obtained. The exposed backups allowed them to download firewall configurations from SonicWall’s cloud environment. The investigation revealed no evidence of exploitation of on-premises firewalls or firmware vulnerabilities; only the cloud backup feature was abused.
No threat actor attribution has been made public, but the breach provides attackers with valuable insight into network architectures, making spear-phishing, lateral movement, or VPN abuse more likely.
Detection Guidance
Security teams should verify whether their organization’s SonicWall devices were impacted:
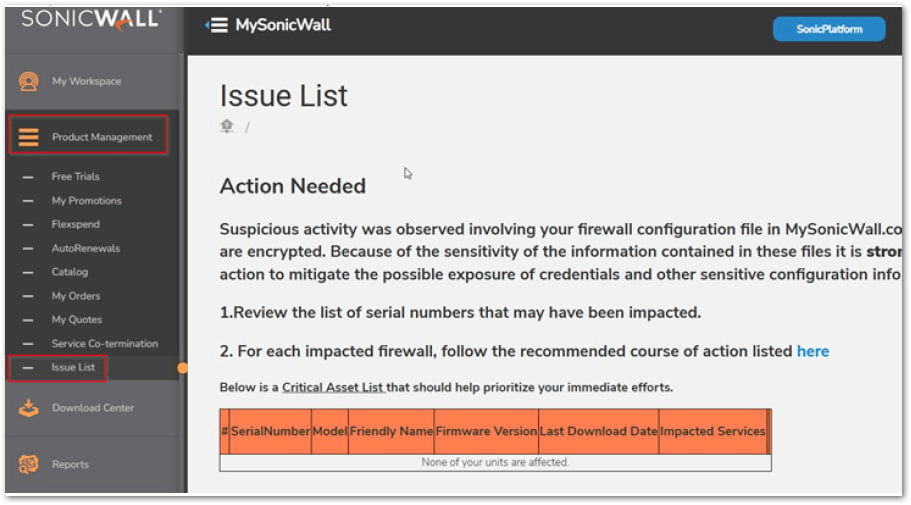
- Check MySonicWall Portal: Log into MySonicWall → Product Management → Issue List. Impacted devices will be flagged by serial number.
- Backup File Review: If backups are visible in the portal, assume those configurations were accessed.
- Log Monitoring: Search for repeated failed authentication attempts or unusual login activity on SonicWall management interfaces.
- Configuration Changes: Monitor for unauthorized configuration modifications or unexpected deletions of backups.
Remediation Guidance
Immediate steps for affected administrators:
- Reset All Credentials: Change all passwords and shared secrets, including admin logins, VPN pre-shared keys, LDAP/RADIUS/TACACS+ credentials, and API tokens.
- Rotate All Keys: Replace all stored keys and secrets that may appear in configuration files.
- Delete Cloud Backups: Remove all cloud backups from MySonicWall and create new backups only after all credentials have been rotated.
- Recreate Backups Securely: Store backups locally or in isolated environments instead of SonicWall’s cloud.
- Follow SonicWall’s Playbook: Use the official remediation guidance and automated tools from SonicWall’s advisory.
Recommendations for Security Teams
- Prioritize Impacted Devices: Treat all firewalls with cloud backups as potentially compromised.
- Monitor Network Behavior: Watch for abnormal connections or new VPN tunnels based on old configurations.
- Harden Firewall Management: Restrict access to management interfaces and enforce multi-factor authentication (MFA).
- Review IR Plans: Update incident response playbooks to account for exposed firewall configurations.
- Evaluate Cloud Security: Review all cloud-based services for similar API exposure or weak authentication controls.
Timeline of Events
- Sept 17, 2025: SonicWall disclosed unauthorized access to MySonicWall cloud backups, initially estimating <5% impact.
- Sept 22, 2025: CISA and the U.S. EPA issued alerts urging customers to reset credentials.
- Oct 8, 2025: SonicWall completed its Mandiant-led investigation, confirming all cloud-backup customers were affected.
External References
What Security Teams Should Do Next
The SonicWall cloud backup breach serves as a wake-up call for organizations relying on vendor-hosted configuration storage. Even though credentials were encrypted, exposing complete firewall blueprints gives attackers insight into your defenses. Verify which devices are affected, rotate every credential, and keep future backups offline or in hardened environments to eliminate residual risk.




